Requirements: Active Directory Domain Services configured.
Installation and Configuration of Certification Authority
-
Install Active Directory Certificate Services:
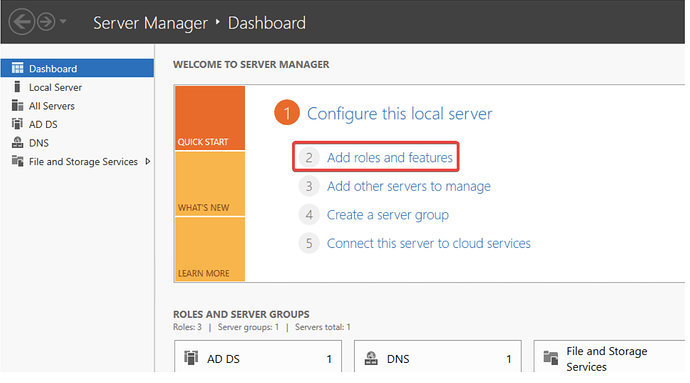
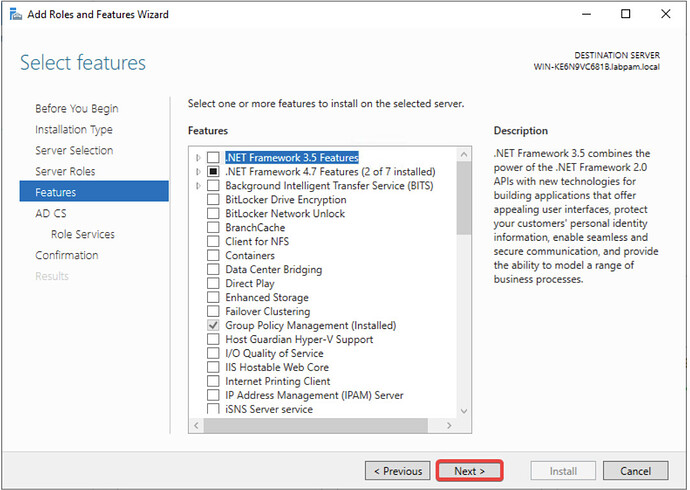
- On the Windows Server machine, open the Server Manager → Add Roles and Features.
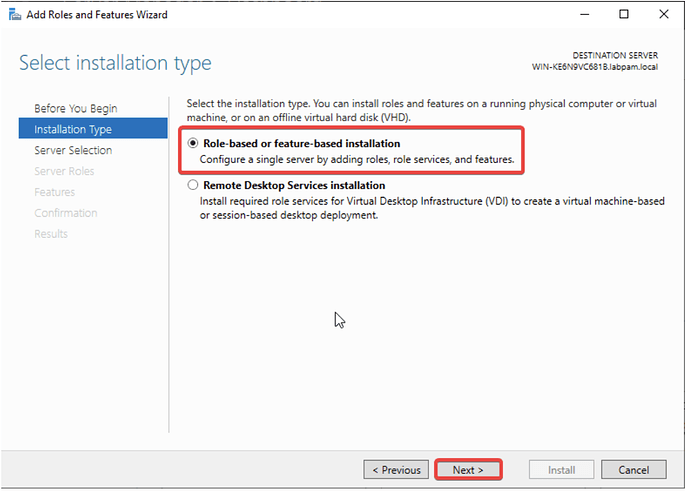
- Click Next until you reach the “Role-based or feature-based installation” option, select it, and click Next.
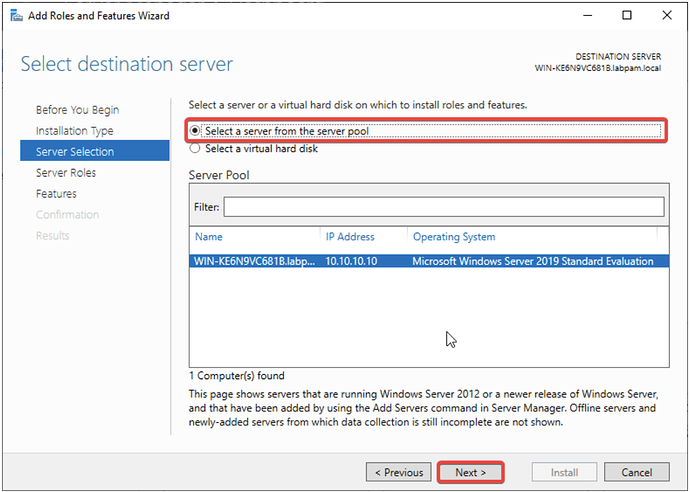
- Select your LDAP server from the list and click Next.
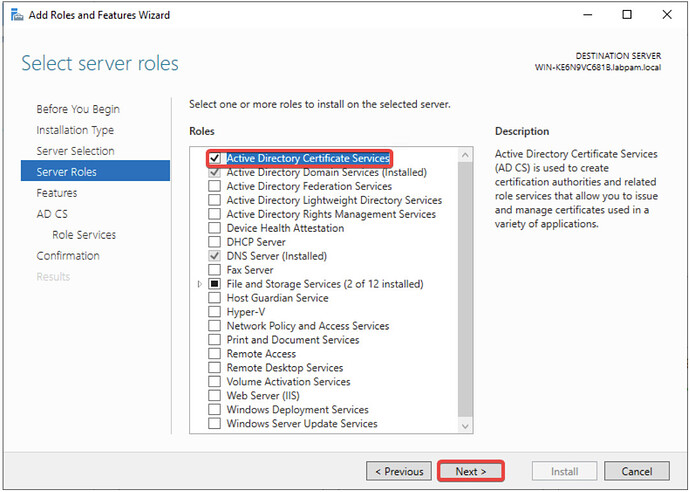
- Check Active Directory Certificate Services, confirm dependencies by clicking Add Features, and click Next.
- Without selecting anything in the Features list, click Next.
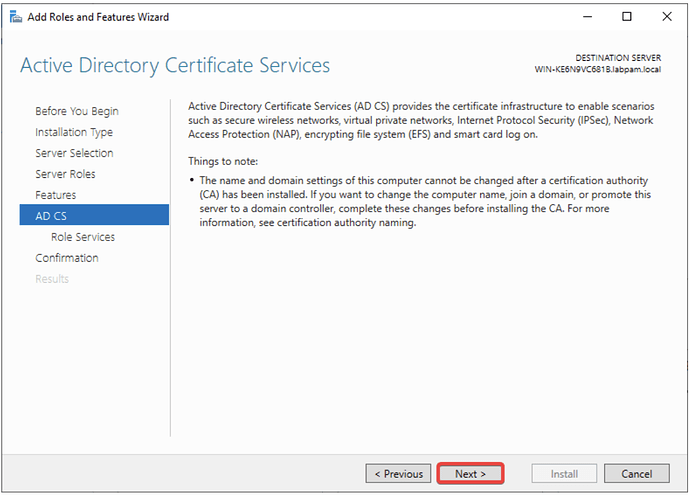
- In the “Active Directory Certificate Services (AD CS)” section, click Next.
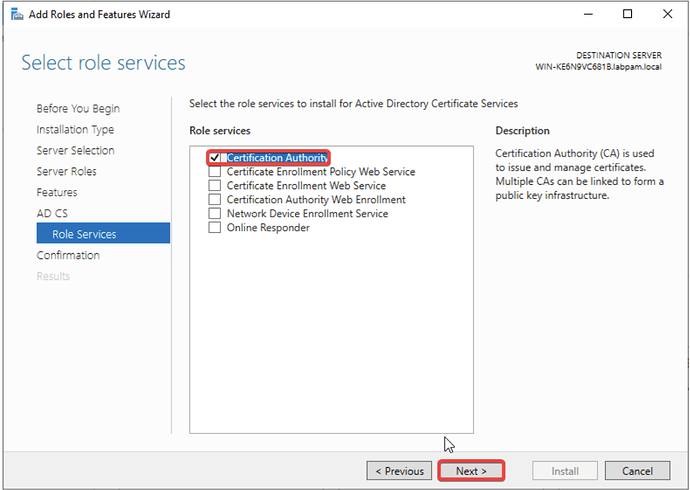
- Check Certification Authority and click Next.
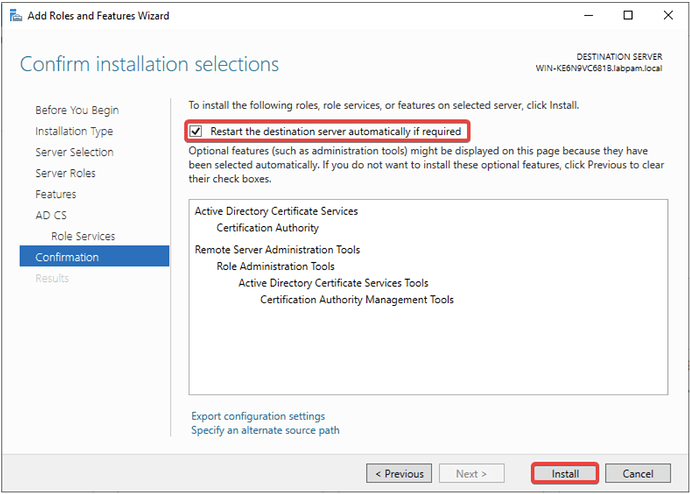
- Confirm automatic restart if requested, and click Install.
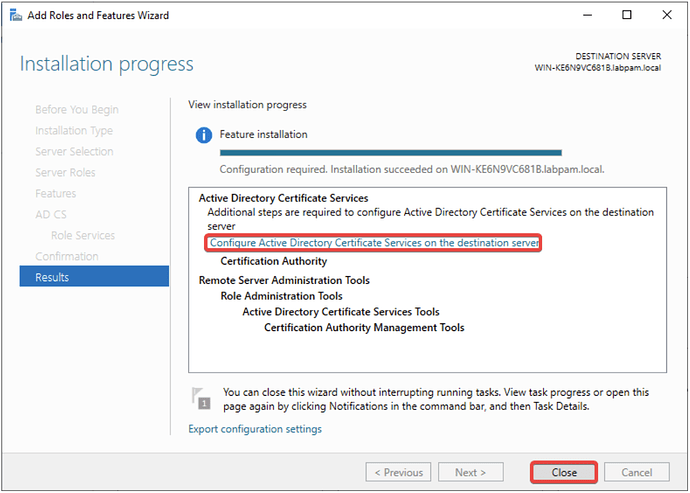
- Click on Configure Active Directory Certificate Services on Destination Server and then Close.
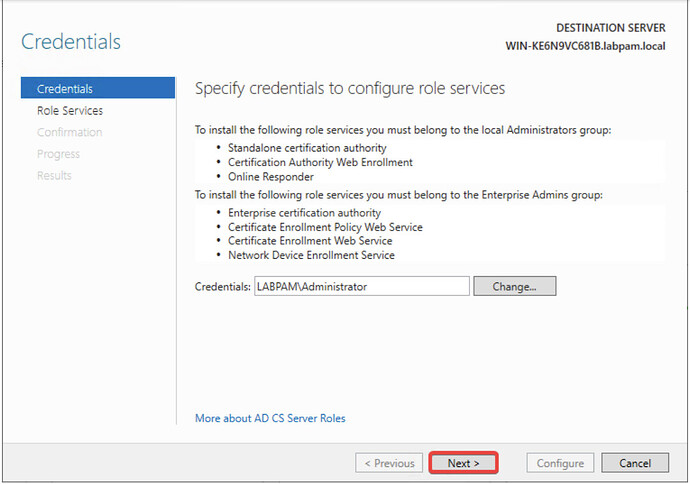
- Ensure the current user belongs to the local Administrators group. Click Next.
Recommendation: Use the Administrator user.
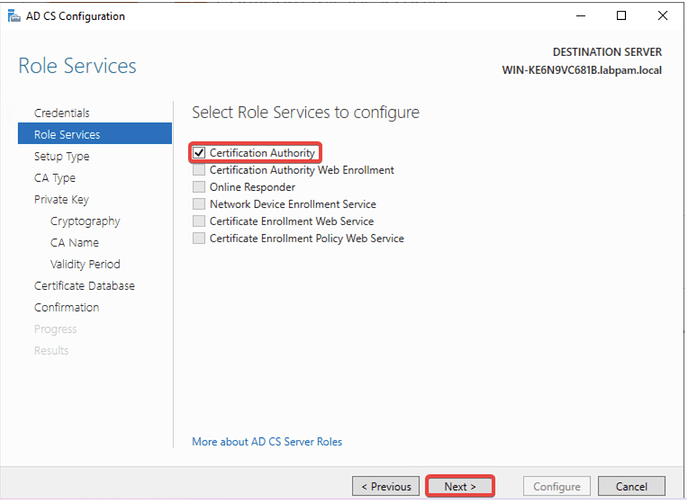
- Check Certification Authority and click Next.
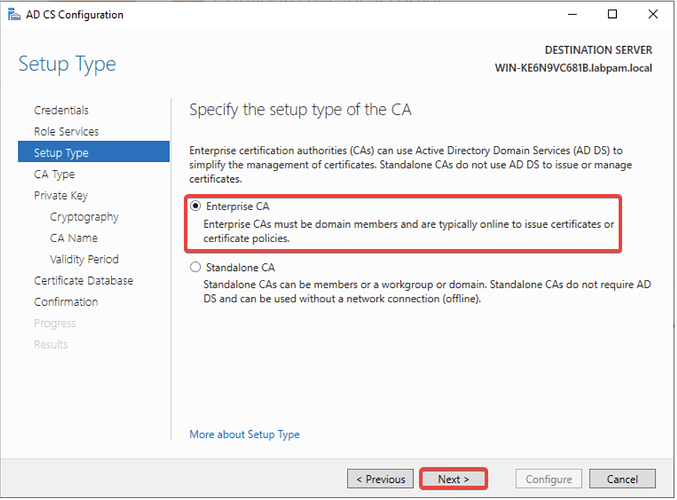
- Choose Enterprise CA and click Next.
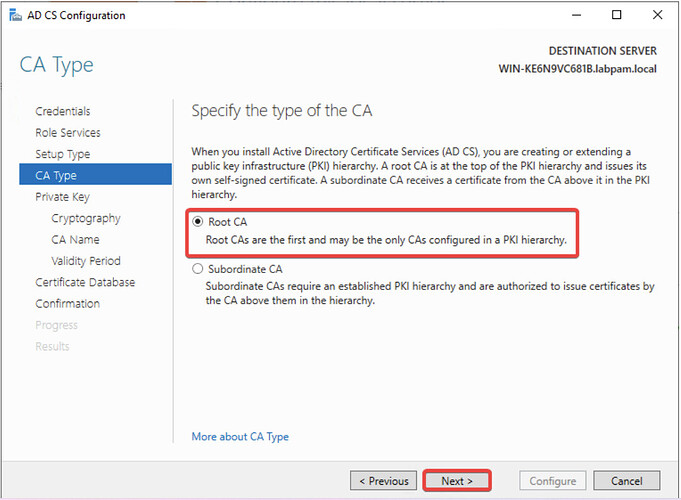
- Select Root CA and click Next.
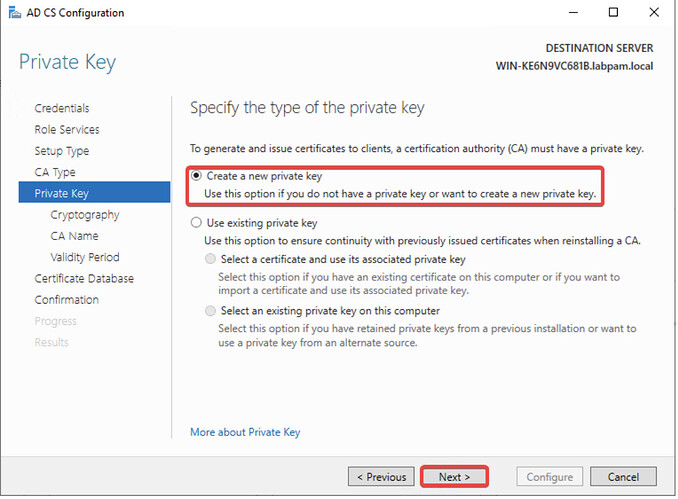
- Choose Create a new private key and click Next.
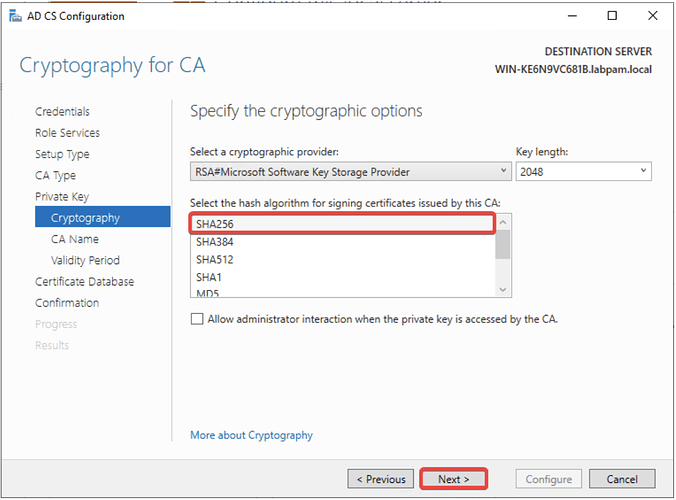
- Select the hash algorithm SHA256 and click Next.
Recommendation: Use the latest available hash algorithm.
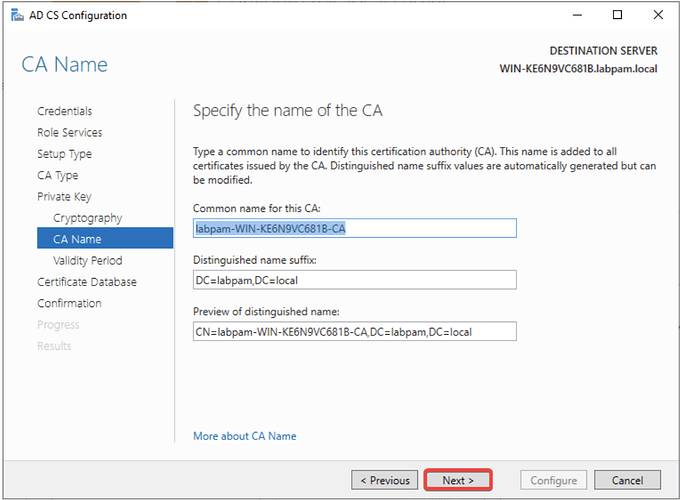
- Click “Next” again.
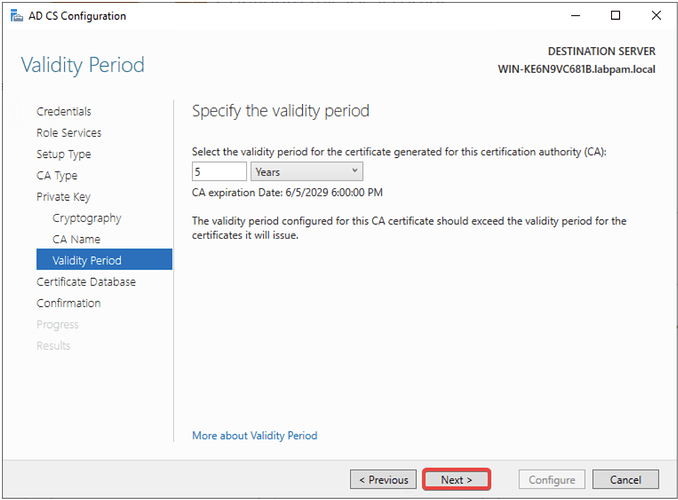
- Specify the certificate validity (default of 5 years) and click Next.
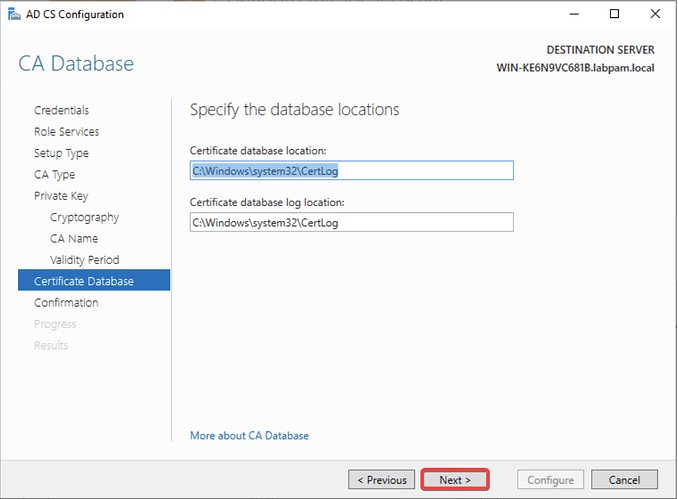
- Select the default database location of the CA and click Next.
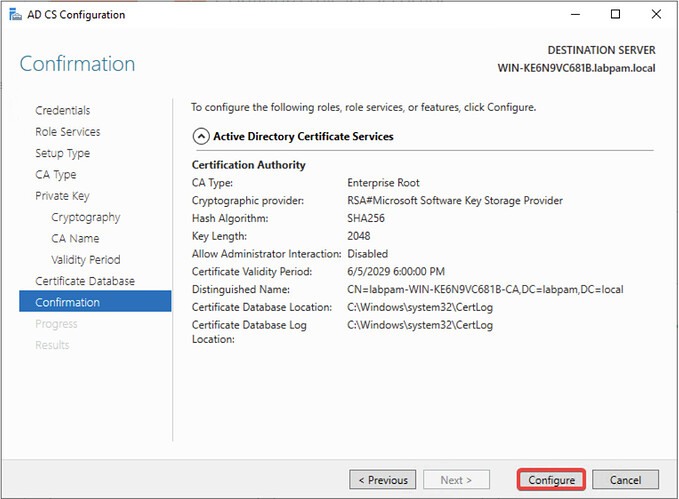
- To confirm, click Configure.
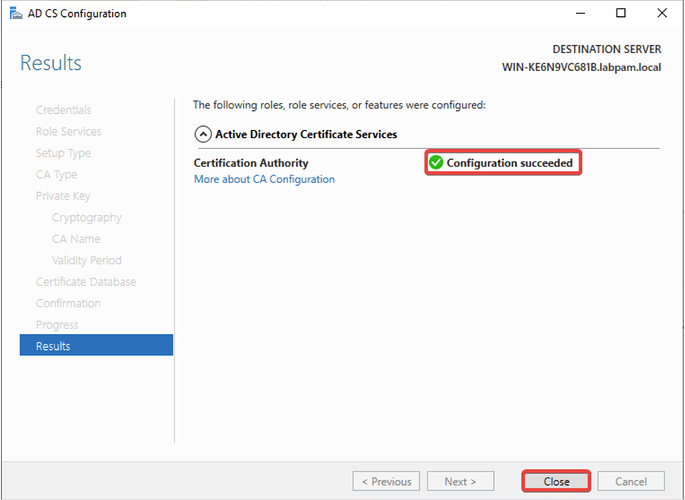
- Finally, click Close.
- On the Windows Server machine, open the Server Manager → Add Roles and Features.
-
Creating a Certificate Template:
- Press Windows Key + R and run the command certtmpl.msc.
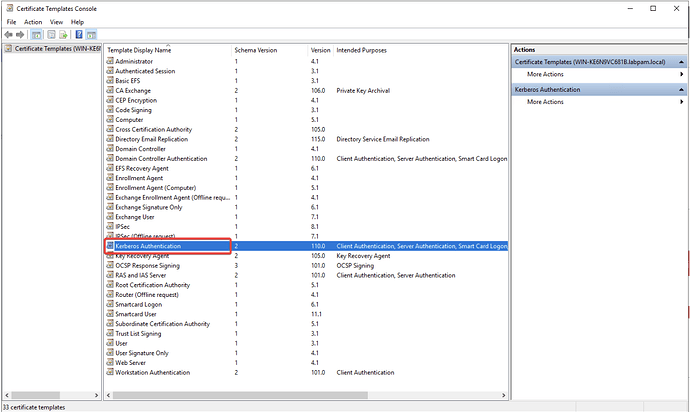
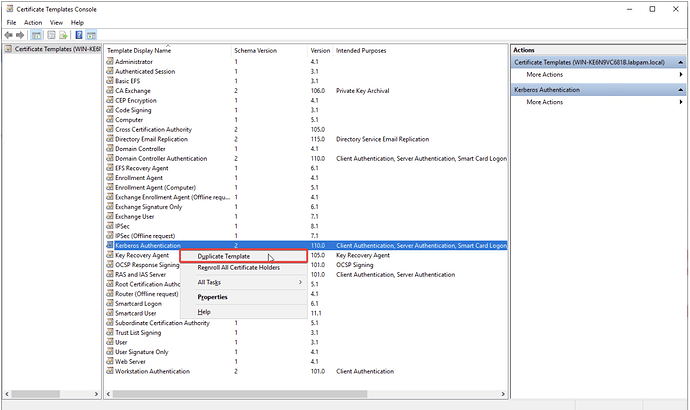
- Find the Kerberos Authentication template, right-click on it and select Duplicate Template.
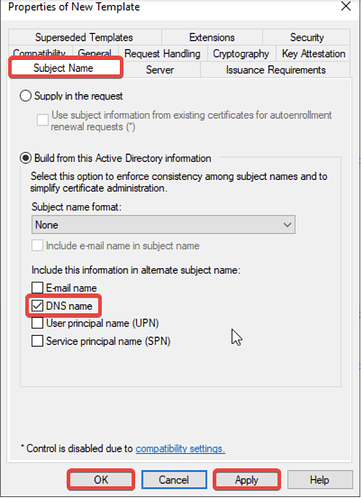
- In the “Properties of New Template” window, configure according to your requirements.
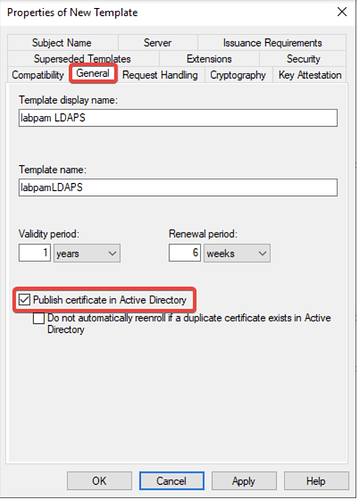
- In the General tab, enable Publish certificate in Active Directory.
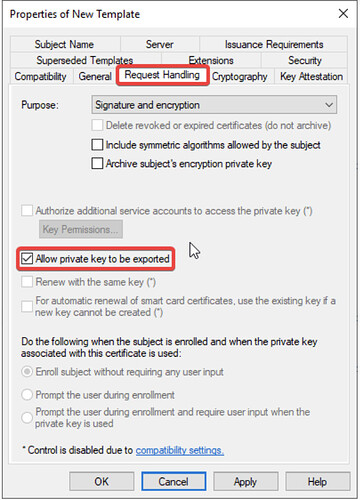
- In the Request Handling tab, check Allow private key to be exported.
- In the Subject Name tab, select the DNS Name format, and click Apply and OK.
- Press Windows Key + R and run the command certtmpl.msc.
-
Issuing the Certificate Template:
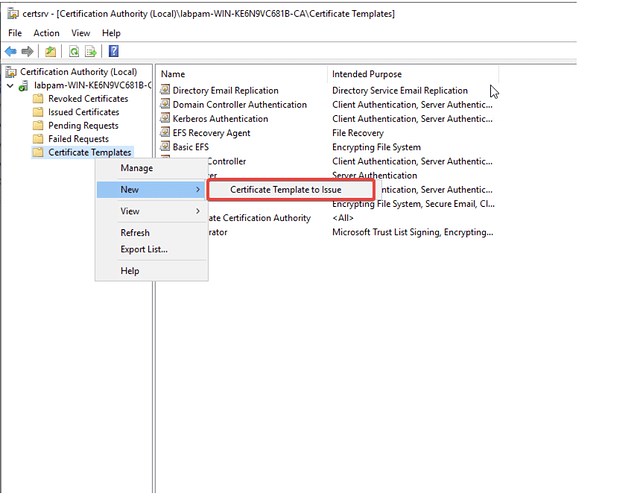
- On the Start menu, type Certification Authority, after it is open, right-click on Certificate Templates and select New → Certificate Template to Issue.
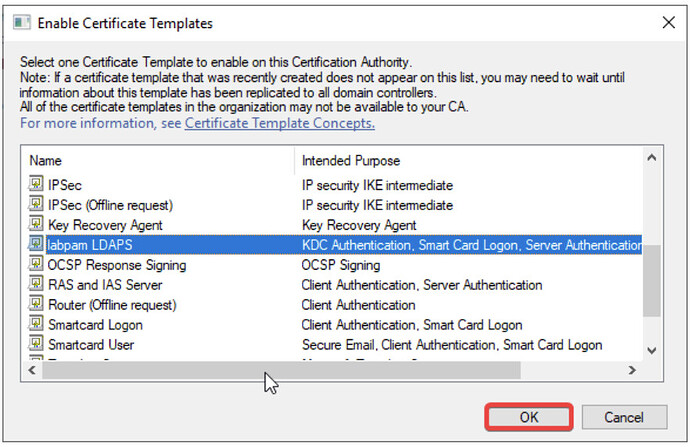
- Select your recently created template and click OK.
- On the Start menu, type Certification Authority, after it is open, right-click on Certificate Templates and select New → Certificate Template to Issue.
-
Requesting a New Certificate:
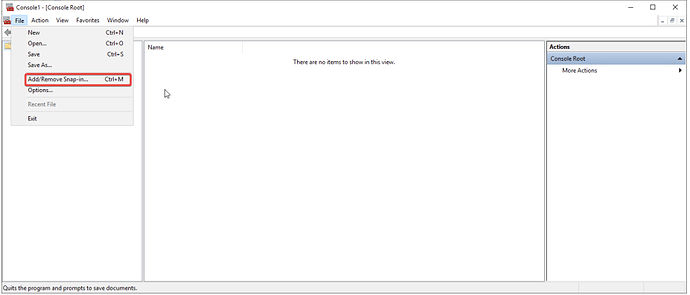
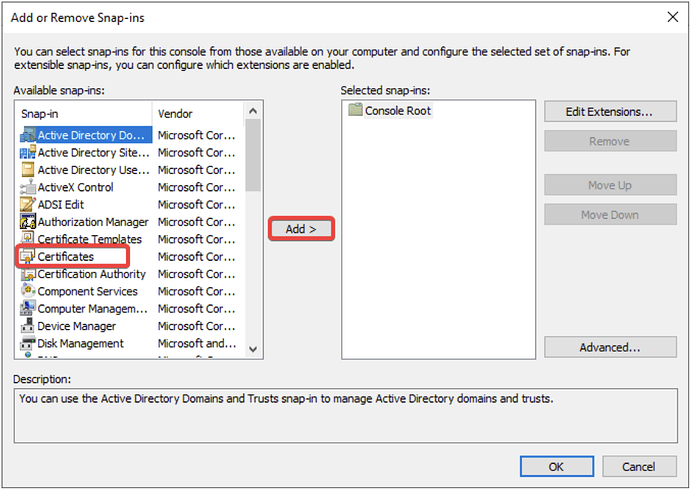
- Press Windows Key + R, run the command mmc, go to File → Add/Remove Snap-in.
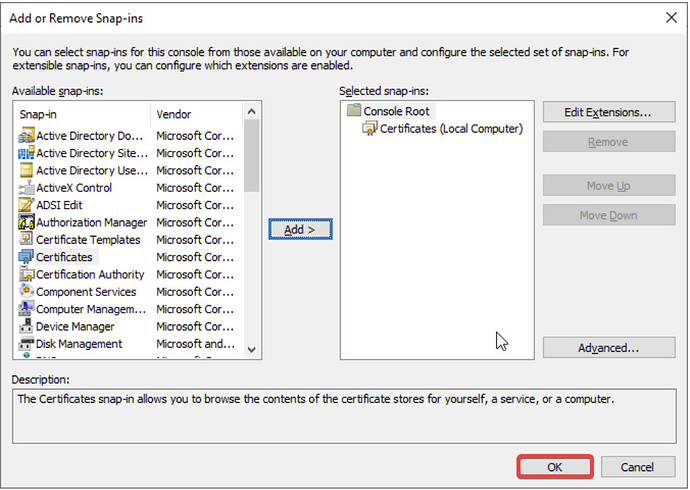
- Select Certificates, click Add.
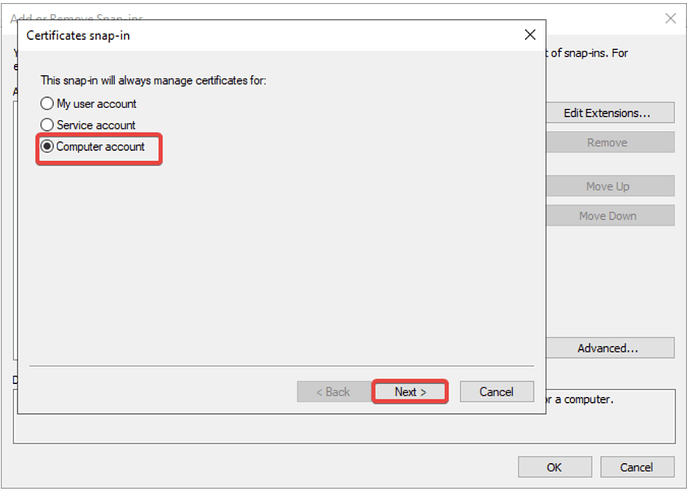
- Choose Computer account and click Next.
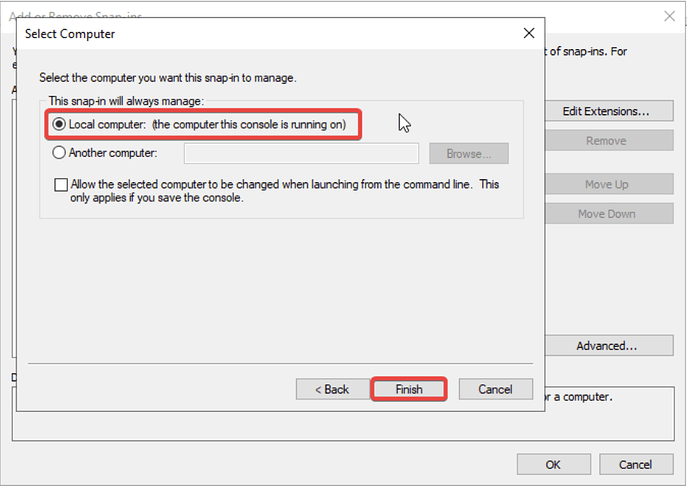
- Select Local computer and click Finish. Click OK.
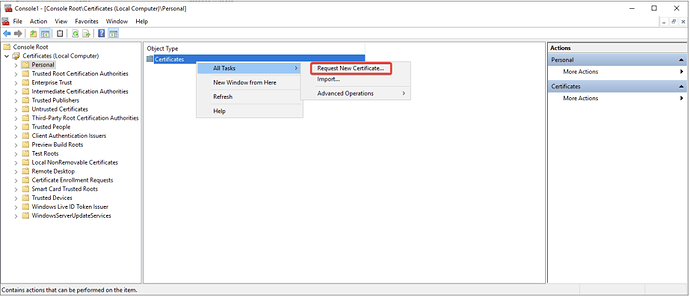
- In the Console, go to Certificates (Local Computer) > Personal, right-click on Certificates, select All Tasks and click Request New Certificate.
- Click Next, and again Next.
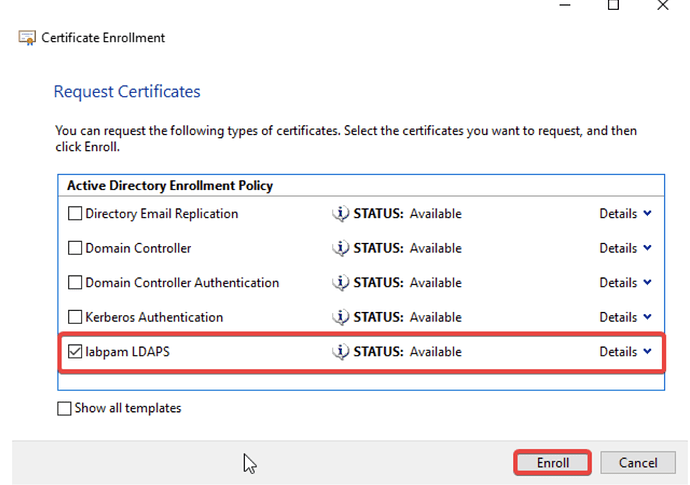
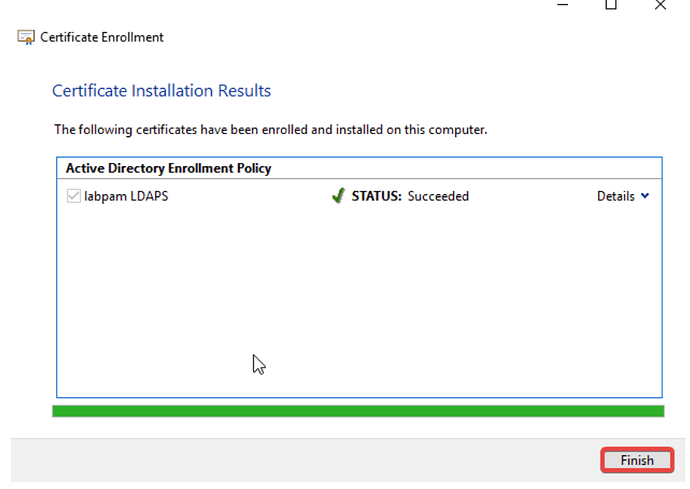
- Select your certificate and click Enroll. Click Finish.
- Press Windows Key + R, run the command mmc, go to File → Add/Remove Snap-in.
-
Exporting the Certificate:
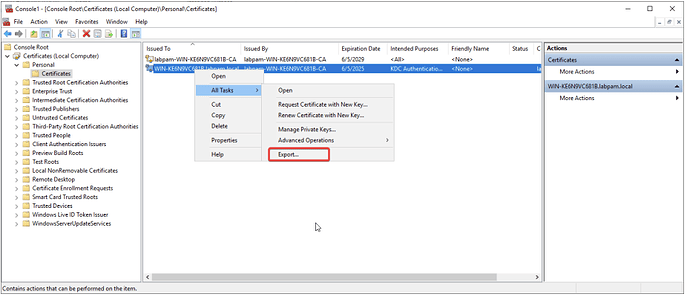
- Right-click on the newly generated certificate select All Tasks → Export.
- Click Next.
- Check Do not export the private key and click Next.
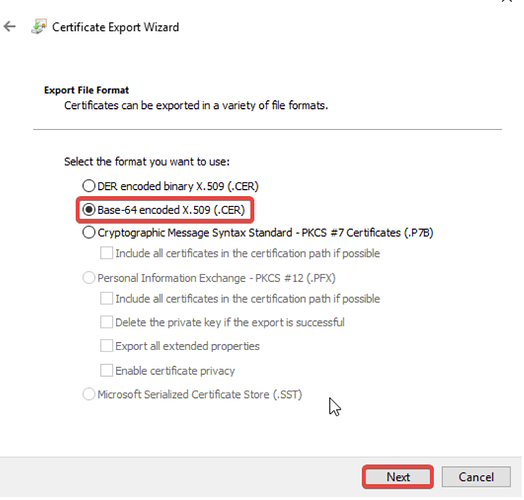
- Choose the file format Base-64 encoded X.509 (.CER) and click Next.
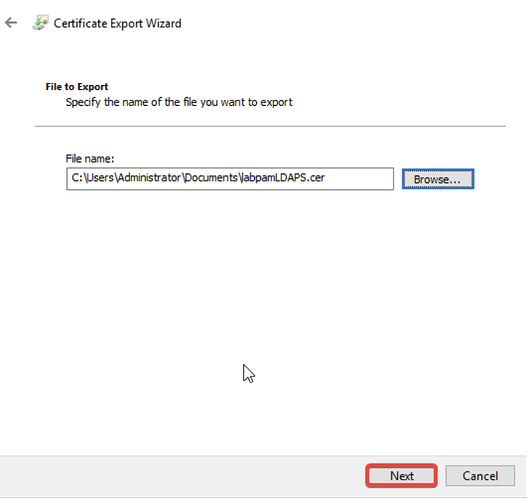
- Select the path to export the .CER file and click Next.
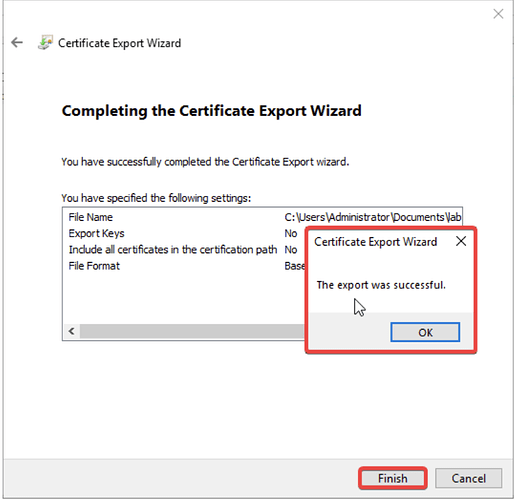
- Click Finish to complete the export. A confirmation message “The export was successful.” will appear if everything is correct.
- Right-click on the newly generated certificate select All Tasks → Export.
-
Testing the LDAPS Connection:
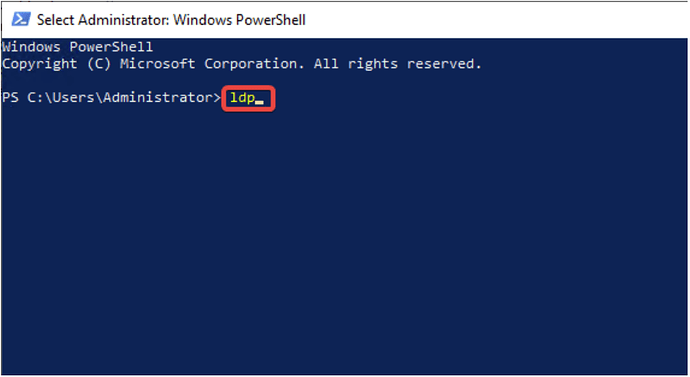
- Open PowerShell with administrator privileges and type the command ldp, then press Enter.
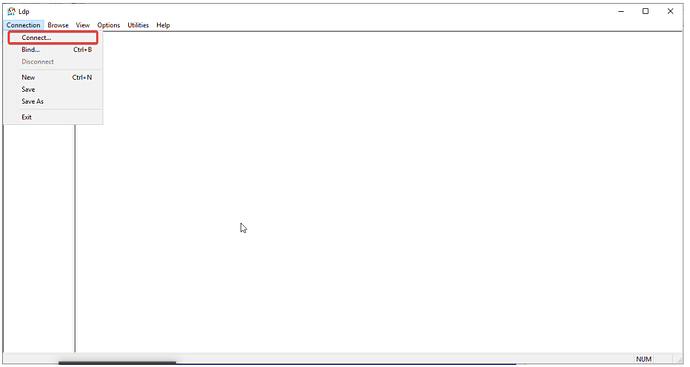
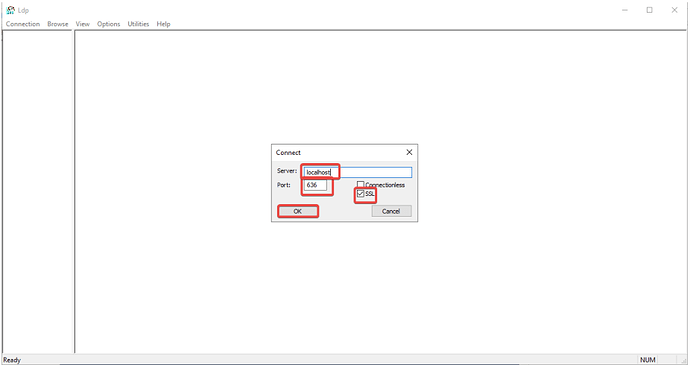
- In the new window, go to Connection → Connect….
- Enter the host, port 636, check the SSL option, and click OK.
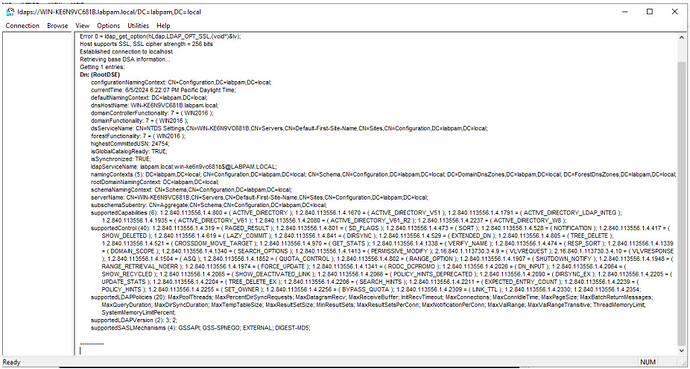
. - If the configuration is successful, a log of the connection to the server via LDAPS will be displayed.
- Open PowerShell with administrator privileges and type the command ldp, then press Enter.
After these configurations, you will be able to set up LDAPS between the Windows Server AD DS and applications such as senhasegura.