Enable Windows RM
- Windows RM operates in two modes: HTTP or HTTPS. To activate Windows RM, simply execute the following command in PowerShell (with administrative privileges):
winrm quickconfig
- After that, to use it via HTTP, execute the following commands:
Set-Item -Path WSMan:\localhost\Service\AllowUnencrypted -Value $true
Restart-Service WinRM
- To enable Windows RM with a secure SSL connection via HTTPS, you can follow the documentation provided here.
Create the Necessary Credentials
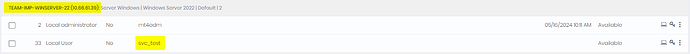
You need to create two credentials: the domain credential, linked directly to the domain controller, and a local credential (created only on the senhasegura platform) related to the target device, as shown below:
The domain credential will have its password rotated on the DC (Domain Controller) and, after that, the local credential linked to the device is used to input the new password into the related tasks
Note: The device needs to have Windows RM connectivity enabled on port 5985 (HTTP) or 5986 (HTTPS).
Create the Template to Change the Password in Tasks
To create a new template, follow this path: Executions → Settings → Template → Create New
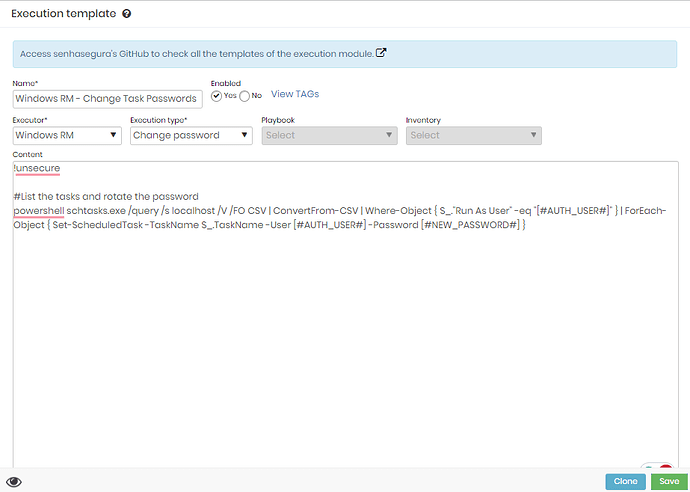
!unsecure
# List the tasks and rotate the password
powershell schtasks.exe /query /s localhost /V /FO CSV | ConvertFrom-CSV | Where-Object { $_."Run As User" -eq "[#USERNAME#]" } | ForEach-Object { Set-ScheduledTask -TaskName $_.TaskName -User [#USERNAME#] -Password [#NEW_PASSWORD#] }
The !unsecure at the beginning will only be used if the execution is via HTTP. Below is the image of the ready template:
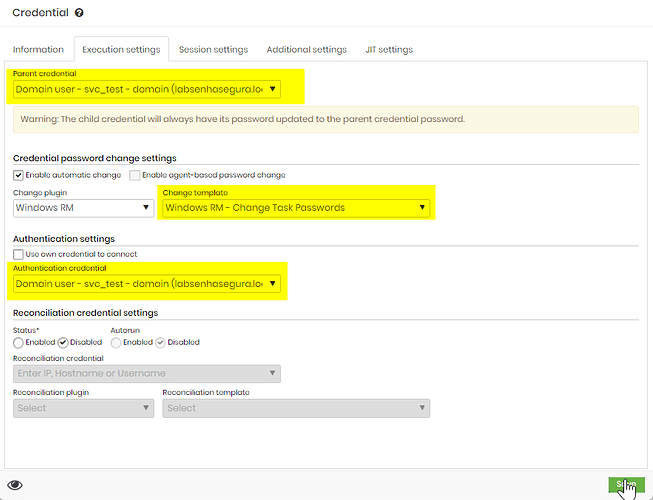
Enable Password Rotation and and Set The Father Credential
In the domain credential, the primary one, there’s no need to change anything in the password execution as it can be rotated with LDAPS.
Now, in the local credential linked to the device, you will activate automatic password change using the template created to rotate tasks, and will select the primary credential as the Parent, as shown below:
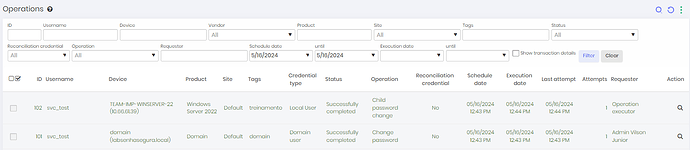
Testing and Results
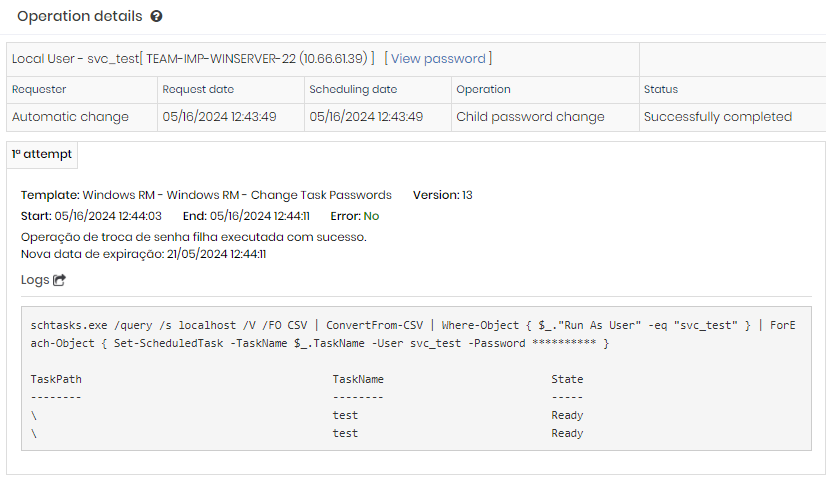
Now, whenever senhasegura rotate the password for the tasks, always updating them with the same password, as can be seen below:
The result of the PowerShell execution: