In senhasegura, the functionality to define an exclusive owner for an SSH credential or key provides additional control over access and use of these resources. This configuration is essential for the security of operations that require strict access control. Below is the process for configuring an exclusive owner within the additional configurations of SSH credentials or keys.
Process for Configuring an Owner for SSH Credentials or Keys:
- Access to Credential Settings:
-
Navigate to PAM Core in senhasegura.
-
Go to the Credentials section and select SSH Keys. Within this section, access the corresponding subsection for SSH Keys.
- Configuring the Owner in the Credential:
-
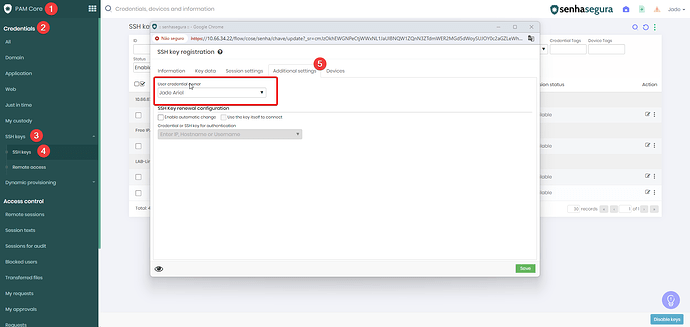
When creating a new SSH key or editing an existing one, click on the Additional Settings tab.
-
Here, you can configure a specific user as the owner of the credential. This user will be designated as the only one with permissions to retrieve the key, view the password, and use it for proxy sessions.
- Exclusivity and Access Restrictions:
- With this configuration, only the designated owner will be able to effectively use the SSH credential or key. Other users, even if they have visibility of the key, will not be able to use it to establish sessions unless they have permission to edit the credential and change the owner.