First, you will need an intermediary device to send requests to the Azure environment. In my case, I used a Debian 10.
In order to be able to communicate with Azure, it is necessary to install its CLI, for that, follow the supplier’s official step-by-step:
After that, log in to the Azure account responsible for executing the requests and with the appropriate permissions as follows:
Updating or creating a new secret through DevOps Secret Manager
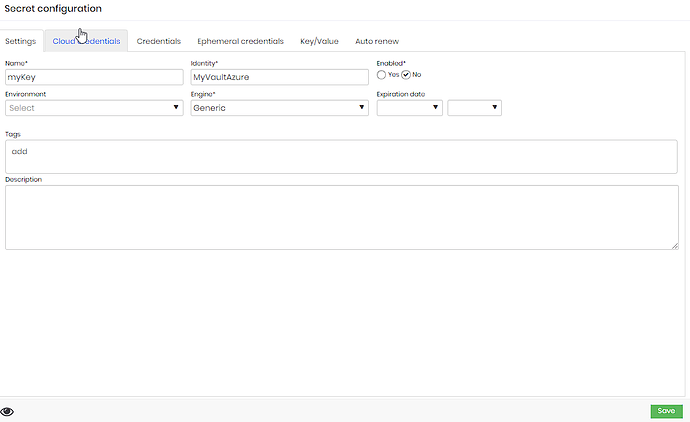
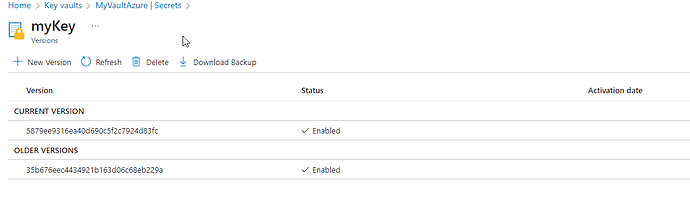
We have the following configuration below, where “myKey” is the name of my secret and “MyVaultAzure” is the name of my Azure Vault.
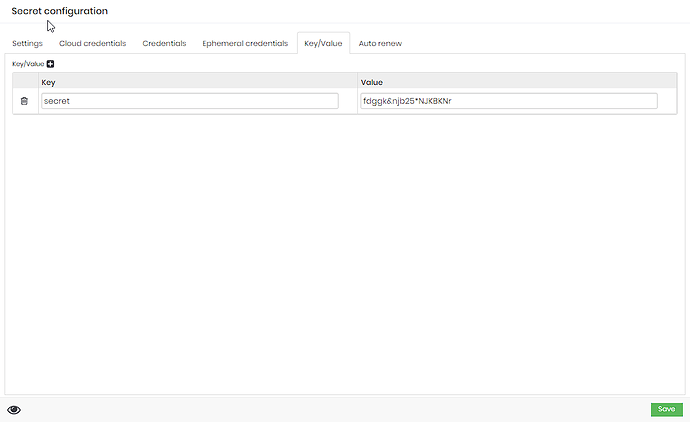
As a value, we have a key/value entity, where the state of a file that has a json with sensitive information is represented:
Creating the automation
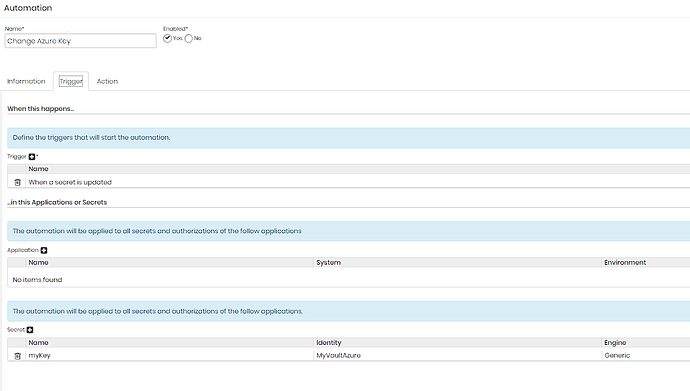
We will have two automations, one that will update the secret value in Azure whenever my secret is changed and another that will delete the secret in Azure when it is inactivated in senhasegura.
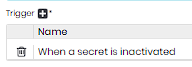
As an update trigger we have:
The same logic must be followed for inactivation, but inserting the item below:
Templates for actions
Template for updating/rotating based on a file:
expect "*$"
exec "az keyvault secret set --name [#SECRET_NAME#] --vault-name [#SECRET_IDENTIFIER#] --file .secret.json --encoding base64"
expect "*$"
Template for updating/rotating based on a value:
expect "*$"
exec "az keyvault secret set --name [#SECRET_NAME#] --vault-name [#SECRET_IDENTIFIER#] --value YourValue"
expect "*$"
Template for deletion:
expect "*$"
exec "az keyvault secret delete --name [#SECRET_NAME#] --vault-name [#SECRET_IDENTIFIER#]"
expect "*$"
IMPORTANT: The tag values are equivalent to the values filled in the secret register, where secret name represents the secret and my Azure Vault identifier.
Examples
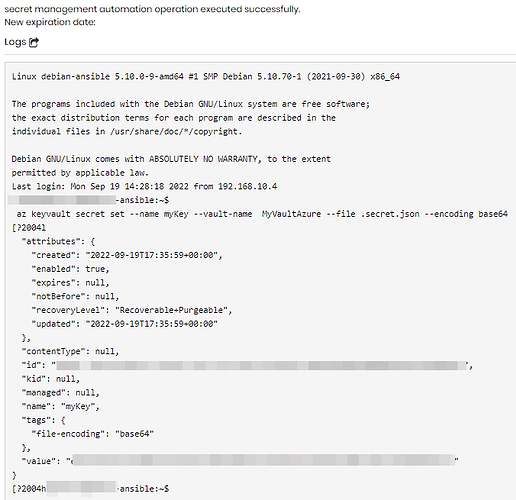
Result when rotating a secret:
In Azure:
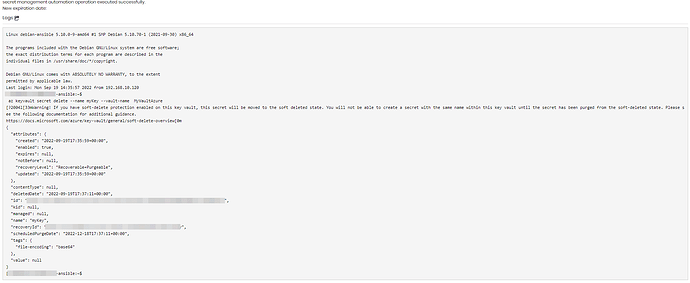
Deleting a secret: