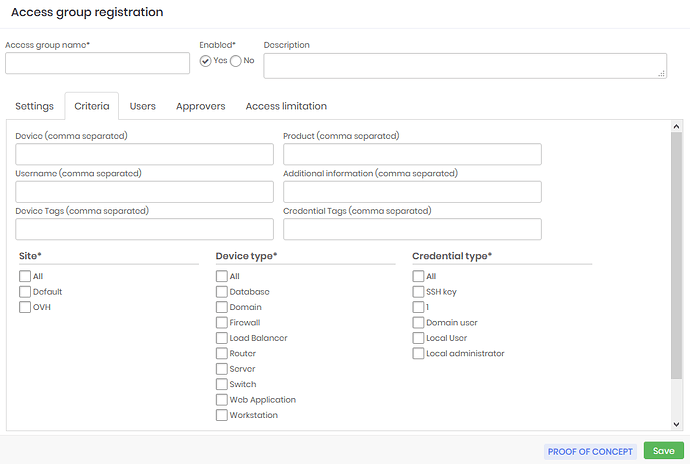
Inside the Access Group configuration on the Criteria tab, you can configure the Access group segregation. Besides the information about Site, Device Type, and Credential Type, you can use tags to further segregate the access group.
These fields are free text fields, and you can use the wild card character which is the asterisk (*) in any part of these fields, lets’s see examples of the use this wildcard have.
- As an example in the Device field:
win* = This will filter all devices whose hostnames start with ‘win’
*win * = This will filter all devices whose hostnames have ‘win’ in any part of its hostname.
win*-server = This will be all devices that start with ‘win’ and ends with ‘-server’.
Another special value that can be used is the mask [username#], which will replace the username of the account which is logged on senhasegura and that is asking to see a device/credential.
- As an example in the Username field:
[username#] = Makes that the user can only see credentials that have the same username as his own.
[username#]-adm = Only credentials that have the composition of the requester’s username and the suffix -adm will be shown.
[username#]* = Will show credentials that have the requester’s username and anything else after it.