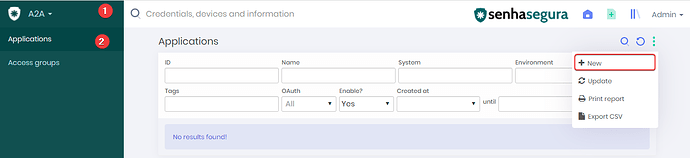
1. Access the A2A>Applications and on the right menu click on new.
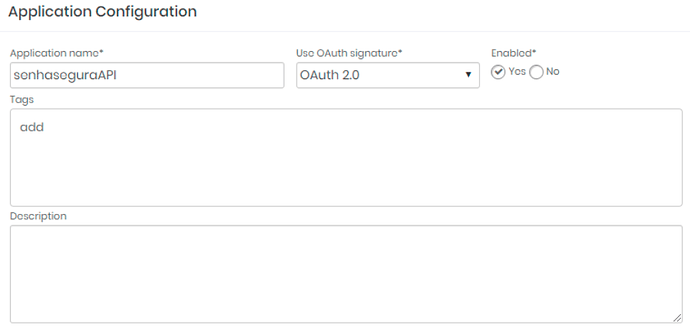
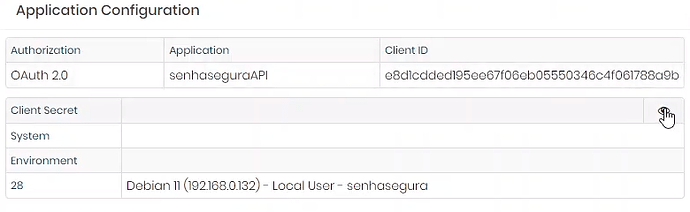
2. On the new screen, define the application name and under “Use OAuth signature” select ‘OAuth 2.0’, a description and tags for targeting can also be added.
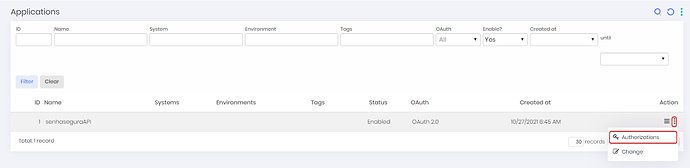
3. To add authorizations, click on the three dot icon and go to 'Authorization s’.
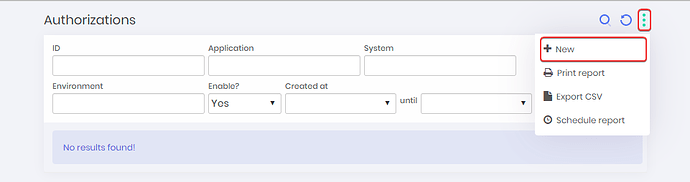
4. On the new screen click on the three dots icon and click on ‘New’.
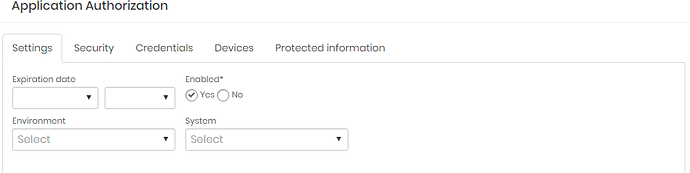
5. In ‘Settings’ the expiration date will be defined, if the 'Expiration date’ field is left blank, the authorization will not have an expiration date.
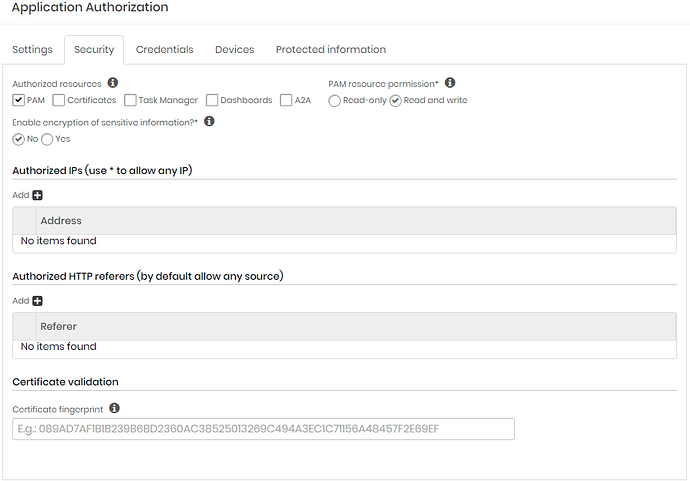
6. In the tab “Security” will be defined which modules the API key will have access, if it is for querying credential passwords select “PAM”. It will also be defined if it can create credentials and devices in ‘Read and write’ or read only in “Read-only”.
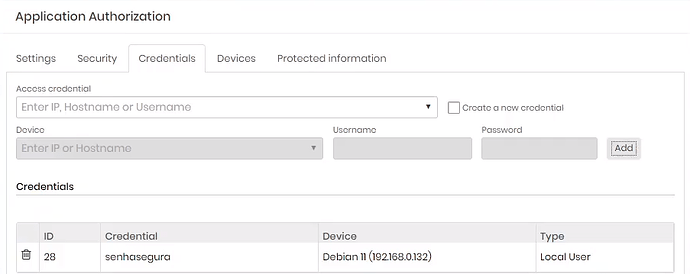
7. In the tab ‘Credentials’ the credential will be added, in this example Debian 11 will have access to ID 28. In the tab “Protected Informations” can be added protected information.
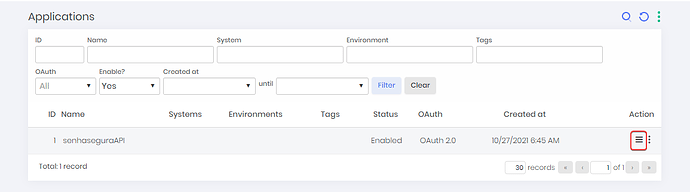
8. To view the API keys that will be used in a request, access the three-bar icon.
9. A new screen will be displayed with the information.
Consumption via cURL
OAuth 1.0 (prior 3.29 version)
Prior 3.29 versions, the OAuth request accepts the Consumer Key and Token parameters directly in URL, and the Signature is not required.
- Request A2A. Replace the fields:
<HOST_SENHASEGURA>
<REQUEST>
<CONSUMER_KEY>
<TOKEN>
curl -s -k "https://<HOST_SENHASEGURA>/<REQUEST>?&oauth_consumer_key=<CONSUMER_KEY>&oauth_token=<TOKEN>&oauth_signature=-"
Example | query id “7” credential password:
OAuth 1.0 (after 3.29+ version)
In 3.29+ versions, the OAuth request require Timestamp, Nonce and Signature in HTTP Header.
Reference: OAuth Core 1.0a
Below, is shown how to create the OAuth Signature based on Linux:
- Create
Timestamp,NonceandSignature. Replace the fields:
<HTTP_METHOD>
<HOST_SENHASEGURA>
<API_ENDPOINT>
<CONSUMER_KEY>
<CONSUMER_SECRET>
<TOKEN>
<TOKEN_SECRET>
export HTTP_METHOD="<HTTP_METHOD>"
export HOST_SENHASEGURA="<HOST_SENHASEGURA>"
export API_ENDPOINT="<API_ENDPOINT>"
export REQUEST_URL="https://${HOST_SENHASEGURA}${API_ENDPOINT}"
export CONSUMER_KEY="<CONSUMER_KEY>"
export CONSUMER_SECRET="<CONSUMER_SECRET>"
export TOKEN="<TOKEN>"
export TOKEN_SECRET="<TOKEN_SECRET>"
export OAUTH_NONCE=$(openssl rand -hex 6) # could be any value
export OAUTH_TIMESTAMP=$(date +%s) # could be any value
export REQUEST_URL_URLENCODED=$(echo -n "$REQUEST_URL" | python3 -c 'import sys, urllib.parse; print(urllib.parse.quote_plus(sys.stdin.read().strip()))')
export PARAMS_URLENCODED=$(echo -n "oauth_consumer_key=$CONSUMER_KEY&oauth_nonce=$OAUTH_NONCE&oauth_signature_method=HMAC-SHA1&oauth_timestamp=$OAUTH_TIMESTAMP&oauth_token=$TOKEN&oauth_version=1.0" | python3 -c 'import sys, urllib.parse; print(urllib.parse.quote_plus(sys.stdin.read().strip()))')
export SIGNATURE_BASE_STRING=$HTTP_METHOD'&'$REQUEST_URL_URLENCODED'&'$PARAMS_URLENCODED
export SIGNING_KEY=$CONSUMER_SECRET'&'$TOKEN_SECRET
export OAUTH_SIGNATURE=$(echo -n "$SIGNATURE_BASE_STRING" | openssl dgst -binary -sha1 -hmac "$SIGNING_KEY" | base64)
- Request A2A.
curl --show-error -s --request "$HTTP_METHOD" --location "$REQUEST_URL" --header "Authorization: OAuth oauth_consumer_key=$CONSUMER_KEY, oauth_token=$TOKEN, oauth_nonce=$OAUTH_NONCE, oauth_timestamp=$OAUTH_TIMESTAMP, oauth_signature=$OAUTH_SIGNATURE, oauth_signature_method=HMAC-SHA1, oauth_version=1.0"
OAuth 2.0
- Request Token challenge to receive the dynamic token. Replace the fields:
<CLIENT_ID>
<CLIENT_SECRET>
<HOST_SENHASEGURA>
curl -d "grant_type=client_credentials&client_id=<CLIENT_ID>&client_secret=<CLIENT_SECRET>" "https://<HOST_SENHASEGURA>/iso/oauth2/token" -s --show-error -X POST
Example | returned token:
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImp0aSI6IjY2NDkyMzRiZGQ5NDZlZGVlODQxMWEyMWMzYTAxM2E1OGI1MWExZWZiMDNlZDA2Yzk5ZDYwMGE1ZDlhOWMwYzEyYjExN2E2ZmY2M2E0NzA5In0.eyJhdWQiOiI2Njk5YmE0NTEwYzc4ZjRkMjEwNjcyNmZjM2U5MjIzNzA1ZmY3MTViYSIsImp0aSI6IjY2NDkyMzRiZGQ5NDZlZGVlODQxMWEyMWMzYTAxM2E1OGI1MWExZWZiMDNlZDA2Yzk5ZDYwMGE1ZDlhOWMwYzEyYjExN2E2ZmY2M2E0NzA5IiwiaWF0IjoxNjMyMzMzNzMzLCJuYmYiOjE2MzIzMzM3MzMsImV4cCI6MTYzMjMzNzMzMywic3ViIjoiTnpRd016WWthMFl5UTJ0TFlYcExhM1p5TTB4S1JUVndaRlZQZEVaSGMzUkViV3gyWjJKamFXTnZSMUYzWjBkTlp6MD0iLCJzY29wZXMiOltdfQ.bIr67Hw7poiXnZLomL3nth3K5LscGFSDUvZQrLeCmKereTeysiX0nLfZeAwdM07q-QkabYjMN7rYshXkmR-I9rlrDQpwpM_9QHjqvMwdztgNQLWZxXb5xTrtQMl4jqNAv9eSceo425-Rs0lU58OR9QGruWhfqF1kP5Zy7sUbPaNtOLCdH-tKFEIs-99DfW7aM0m0695awUrs-NZjbjE-JzHtNu1W_HqAHYMLEOK00PDlkWkzWsj59-thK6kNHuphVpVLGbfoWJ5SUMwDhLSy_Mn6Ae8CroWIOb3ZsqHPJFDQ--lq7Inb4sihoSGAksBj7PkVTxr8FZwV5tAYHu0dAg
- Request A2A. Request the fields:
<OAUTH2.0_TOKEN>
<HOST_SENHASEGURA>
<REQUEST>
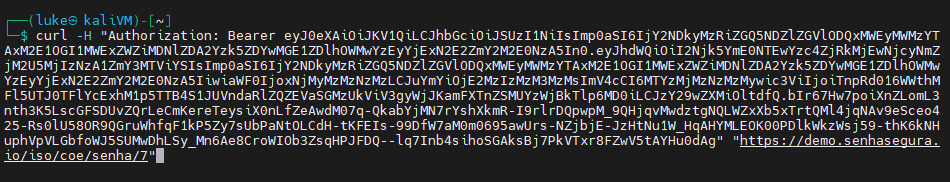
curl -H "Authorization: Bearer <OAUTH2.0_TOKEN>" "https://<HOST_SENHASEGURA>/<REQUEST>"
Example | query id “7” credential password:
Hint: if the SSL error shows up, add -k parameter in the cURL command execution.