Requirements:
- Administrative access on senhasegura to edit the configuration on User Groups.
- Administrative access on Portal Azure to create and assign Roles.
To assign an Access group to users on senhasegura, you must create a group on Azure AD and have the same UserGroup created inside senhasegura. This group will need to be created without spaces and accents.
To assign Roles, it is necessary to create a role inside Azure AD, and this role in Azure AD must have the same name as a Role in senhasegura, without spaces and accents.
To create a role inside Azure AD, you can follow Microsoft’s guide present here:
How to create roles on Azure AD
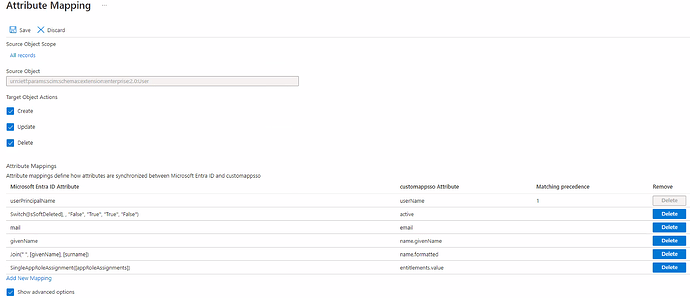
It is also necessary to have the User Mappings configured. For this, click on “Provision Azure Active Directory Users”:
Fill the attribute panel with only the information below:
If the “SingleAppRoleAssignment([appRoleAssignments])” attribute does not exist, you can create it manually by following the point “4.1 Configure User mappings” present in this documentation:
How to create the Configuration for User Mappings
After this, senhasegura can get the correct configurations from Azure AD on the Roles and Access groups. To test the provisioning, go to the SCIM Configuration and choose the ‘Provision on demand’ menu.
On this page, you can manually choose the user you want to provision with senhasegura.