Yes, the “winexesvc.exe” service is officially used by specific senhasegura plugin. The service in question is classified by Sophos as a PUA (Potentially unwanted application), as well as PsExec.
The senhasegura application offers other plugins for to execute discovery and password changes, which not
use the aforementioned service.
Technical Review:
Executions module
The senhasegura’s Execution module perform remote executions on devices managed by the application.
Scan Discovery module
The senhasegura’s Discovery module searches for relevant information for the registration of credentials within the application. Users, groups and hostname are examples of information fetched. These data are retrieved from devices that are within the IP range specified in the application, when you configure a Discovery.
Plugins
In order for remote executions and relevant information to be brought from the Windows devices, the application must communicate with these devices. senhasegura can communicate with these devices through 3 plugins: WinRM (Windows Remote Management), WMI (Windows Management Instrumentation) or RPC (Remote Procedure Call), all provided by Microsoft itself.
The “winexesvc” service is created when the RPC plugin is selected for scanning or password change. The choice of plugin is based on on the ports made available by the managed devices.
winexesvc.exe
After establishing the connection with the Windows device through RPC, the “winexesvc.exe” binary is executed from the senhasegura application, as a way of performing remote commands on the Windows device. The “winexesvc” execution pipeline includes the creation and termination of the “winexesvc” service within the Windows device remote. In this way, the service is active only at the time of execution of a scan or password change, as shown in Figures 1, 2 and 3.
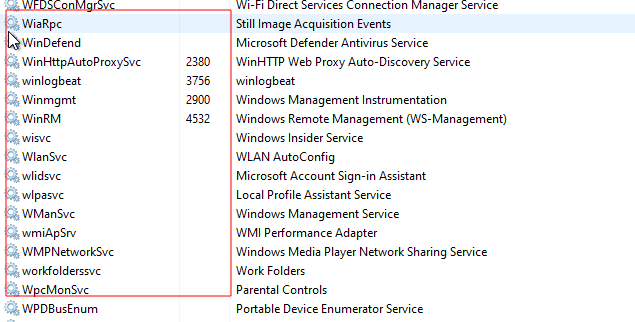
Figure 1 - Before the execution
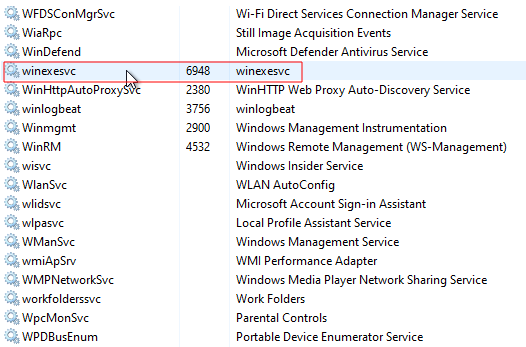
Figure 2 - During the execution
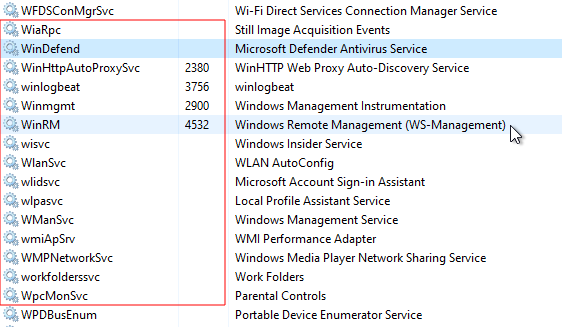
Figura 3 - After the execution
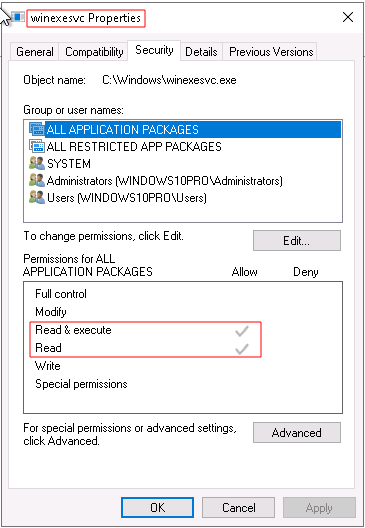
The process “winexesvc.exe” has only read and execute permission, according to Figure 4, necessary for the application to obtain the data previously mentioned.
Figure 4 - Permissions
Sophos
Sophos classifies “winexesvc.svc” as a PUA (Potentially Unwanted Application), as does PsExec. An application detected as PUA is a legitimate application, which was developed for benign use, however it can be used as a malicious tool, just like it is a port scanner.
In this case, it is worth creating an allowlist, which allows this type of interaction only with senhasegura.
Link to Sophos Classification
Alternatives
senhasegura offers 2 other plugins if the execution pipeline using RPC is not adequate to the requirements of the environment. These alternatives are the plugins: f WinRM and WMI, which do not create the related process/service “winexesvc.exe”.